(NFC relay + automated bank fraud)
Summary: A new Android Remote-Access Trojan (RAT) named RatOn has been observed in the wild. Unlike many banking trojans that reuse old code, RatOn is modern and modular combining overlay phishing, an Automated Transfer System (ATS), and an NFC-relay capability that enables in-person payment fraud. While first seen targeting Czech banking and crypto apps, its capabilities make it a serious global threat — including to Indian users, banks and regulators.
What is RatOn - quick overview
RatOn is a purpose-built Android banking trojan,
It steals credentials by overlaying fake login screens, using Android Accessibility permissions to hijack user interaction, automates account takeovers and transfers with ATS features and
performs NFC relay attacks that let attackers proxy contactless payments through an infected phone and a nearby terminal or device. These combined capabilities allow attackers to both remotely drain online accounts and perform in-person payments using victims’ devices.
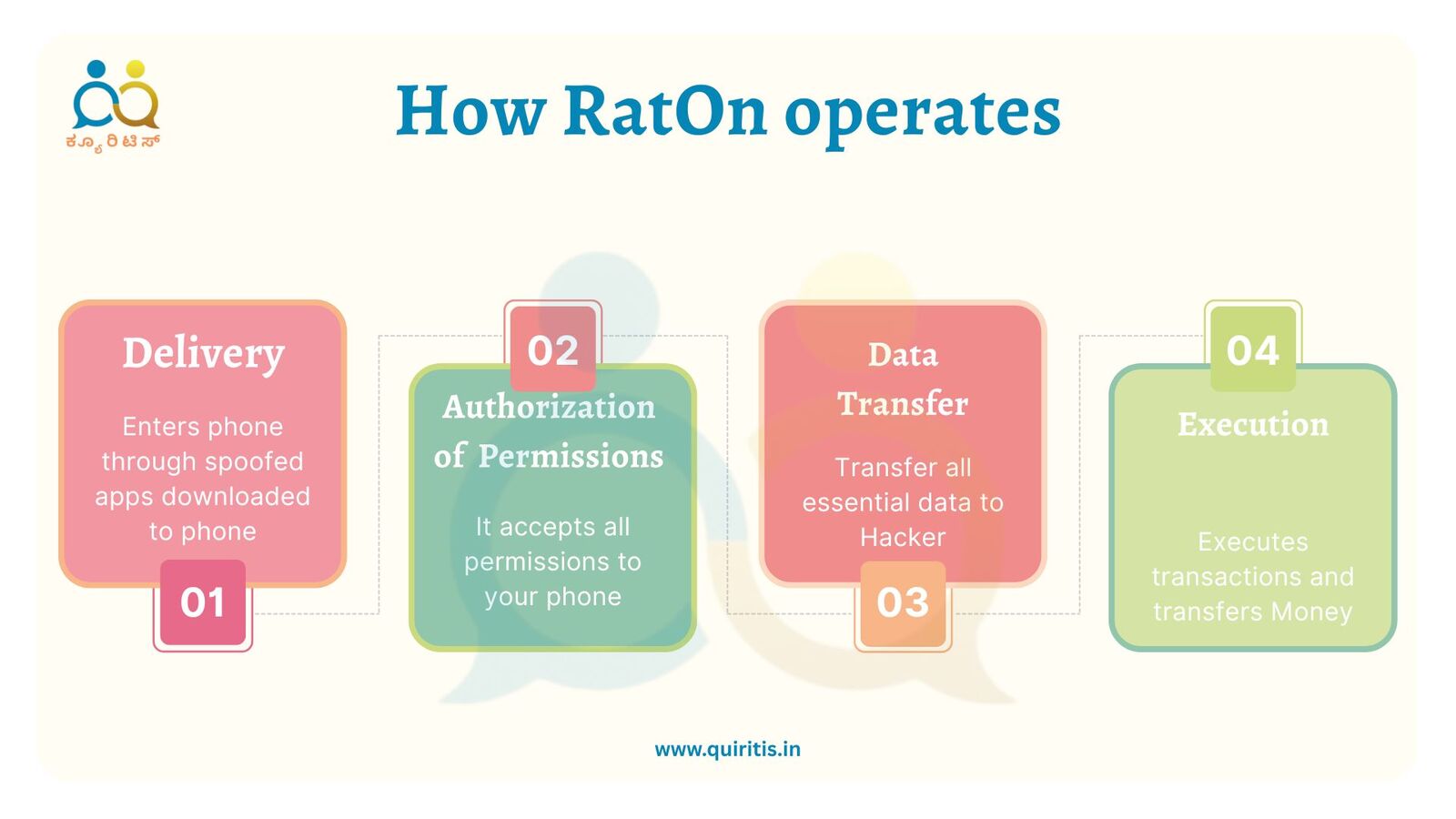
How it spreads and how it operates (technical flow)
Delivery
It is distributed via spoofed app pages and phishing sites (examples reported as fake “TikTok18+” or similarly themed pages). Victims install a malicious APK, often sideloading or clicking a convincing link.
Escalation of permissions
The install requests powerful permissions (Accessibility, overlay, device admin-like controls) so the malware can show fake screens, read/act on the UI, and intercept input.
Modular payloads
Once installed, RatOn downloads additional modules such as an overlay/credential harvester, an ATS module to perform automated transfers, and an NFSkate module to perform NFC relay attacks to capture or transact using contactless payment data.
Execution
Attackers either (a) remotely take over accounts (enter stolen credentials, complete MFA bypass techniques, trigger transfers), or (b) perform in-person NFC relay transactions by placing a compromised phone near a payment terminal or collaborating mule device.
Why RatOn is especially dangerous for finance
Multi-vector fraud it combines remote credential theft + ATS + NFC relay creates new fraud patterns that are harder for banks to detect via single-signal analytics.
Targets crypto wallets and banks: attackers target both traditional banking apps and cryptocurrency wallets, increasing potential financial loss and forensic complexity.
Links to India: regulator posture and similar local incidents
While RatOn was initially reported against European targets, India’s financial ecosystem faces parallel mobile threats and has been active on cyber response.
Indian banking-targeting Android campaigns: security vendors have recently reported Android malware that impersonates Indian banking apps (SBI Card, Axis Bank, IndusInd, etc.) and harvests credentials via phishing/overlay techniques, the same class of attack RatOn uses. This demonstrates that the attack pattern is already effective in India and could be adapted to RatOn-style tooling.
Regulatory focus / advisories: India’s regulators and financial market operators have been issuing advisories and emphasizing stronger cyber posture for the BFSI sector (for example, BSE and CERT-In notices and RBI guidance on stronger cybersecurity and controls). The Reserve Bank of India and market bodies have pushed banks to adopt modern defenses (zero-trust approaches, multi-layer fraud detection) — measures that directly mitigate advanced mobile banking trojans.
CERT-In and Indian banks have published mobile malware advisories (mobile banking trojan families, phishing campaigns) and actively monitor such campaigns. Banks and incident response teams can look for indicators of compromise (IoCs) similar to those published by global researchers for RatOn.
What users should do?
Don’t side load apps or install from unknown websites; use Google Play only (for android users).
Refuse Accessibility permission requests from apps that don’t need them. Accessibility access is a red flag if requested by non-utility apps.
Keep Android updated and enable Play Protect, secure your apps with 2- factor authentication.
