What is Phishing Attacks?
“Phishing” refers to the practice of sending fraudulent messages that is made to look like it has come from an original or a legitimate source. The main intention of this messages is to make a user click on any attachment sent in that message. Once a user clicks that message then the attacker will have access to the users system and he will be able to retrieve any personal information of the user without the user actually noticing.
Learning about this attack is important as this is one of the most used attacks in a everyday basis.
How does Phishing work?
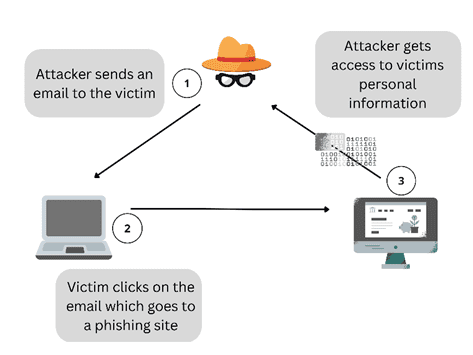
Types of Phishing Attacks
Here are some of the Phishing Attack types that are mostly used,
1. Spear Phishing
2. Smishing
3. Vishing
Spear Phishing
Spear phishing is a form of cyberattack that employs emails, phone calls, or other electronic interactions to target select people or organisations. In comparison to traditional phishing attacks, which send out mass emails with the intention of capturing a few naïve victims, spear phishing attacks are considerably more targeted and towards a specific victim.
Smishing
Smishing is a type of cyberattack that uses text messaging, often known as SMS (Short Message Service), to pressure victims into giving personal information or downloading harmful software. The term "smishing" is the combination of the words "SMS" and "phishing."
Vishing
A type of cyberattack known as "voice phishing" or "vishing," uses phone conversations to trick victims into giving out their personal information. This is done to obtain personal or financial information from the victim or infect their device with malware, the attacker may pose as a reputable company, such as a bank, a government agency, or a tech support firm.
Prevention
·Unexpected emails should be check before opening it.
·Verify the accuracy of the sender's email address and domain name.
·Emails from unidentified sources shouldn't be opened by clicking links or downloading files.
·Hover your mouse over links to see their URLs before clicking them. You will know the exact site to where it is taking you.
·To prevent known vulnerabilities that attackers can exploit, keep your software and operating system updated with the latest security updates.
·Use strong, one-of-a-kind passwords for each of your accounts and turn on two-factor authentication for additional security.
·Inform yourself and others on how to recognise the most recent phishing scams.
·Finally, always remain aware of what has come in your mail or messages. BE AWARE!
